Getting Familiar with Microsoft Azure#
While Azure offers similar resources to other cloud services, the terminology is slightly different. This tutorial covers the basics of working in Azure, whether you’re new to using cloud resources overall or just new to Azure.
Azure Accounts and Subscriptions#
Each individual using Azure has an account. When using Azure through Northwestern, your account is tied to your Northwestern NetID and email, and you use your Northwestern credentials to log in.
To create and use resources, your account needs to be tied to a subscription with associated billing information.
Your account can be linked to multiple subscriptions where you may have permissions to allocate or use resources. You are not necessarily the owner of all subscriptions you can access. The data stored and tasks performed within one subscription are isolated from another.
If you do not yet have access to an Azure subscription, see the steps for Requesting an Azure Subscription.
Azure Portal#
Once you have access to an Azure subscription, log in to the Azure portal using your Northwestern NetID/email credentials at https://portal.azure.com/ .
Home#
When you log in to the Azure Portal with your @northwestern.edu account, you should encounter the Home page. If you ever get lost, click on the triple bar on the top left and select Home to get back here. The triple bar button opens the Portal Menu.
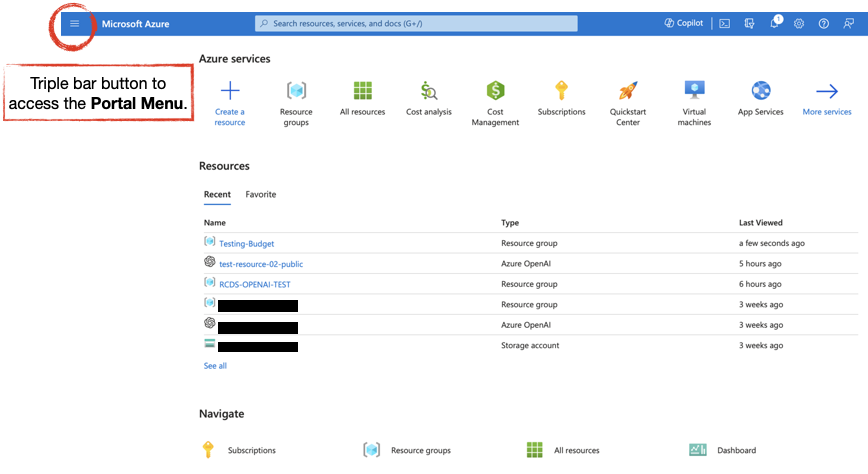
Home may look slightly different depending on whether you’ve used Azure before and what resources you use over time. The Resources section should be empty if you haven’t created any yet. See the Resource and Resource Group section below for more on Resources.
The Azure Home page is different than a Dashboard.
Dashboards#
If you click on the triple bar menu on the top left, you will also see Dashboard as an option. The Dashboard is not your home. The Dashboard is a place to view your Azure resources and applications from different perspectives.
You can have multiple dashboards. At the beginning there is one default dashboard without much in it: a list of resources and of guides. However, you can create personalized dashboards summarizing different elements of your Azure subscription. Azure provides some handy pre-made dashboards: one showing an inventory of all resources accompanied with some statistics about them, one to track different applications, one to track SQL databases, etc.

Managing Subscription Access#
You can add users to your subscriptions by following this Azure documentation that provides instructions on how to assign users roles.
Users with access to your resources may not need direct access to your subscription, for example when calling an AI model or when connecting to a database. Instead, you can provide them with credentials to connect to and use resources that you allocate. Only users who need to create new resources or modify or delete existing resources are likely to need access to your subscription.
When providing access to your subscriptions to others, you must assign them a specific role or roles where they will have clearly defined permissions. Azure has an extensive list of prebuilt roles that you can use. Here is a list of common roles that fit some common resource use cases.
| Role | Can Do | Can’t Do |
|---|---|---|
| Azure AI Developer | Build and deploy AI models, call AI APIs (e.g., Cognitive Services), configure models, monitor performance | Cannot delete or manage the AI service itself, assign roles, or handle billing |
| AzureML Data Scientist | Create, train, and deploy models, run experiments, use datasets, manage compute resources for training, build ML | Cannot manage Azure resources (e.g., workspaces), assign roles, or handle billing |
| Storage Account Contributor | Create, delete, and manage storage accounts, upload or download datasets, manage storage account configurations | Cannot manage non-storage resources, assign roles, or handle machine learning or AI-specific resources |
| Billing Reader | Allows read access to billing data | Cannot manage or modify any resources inside the subscription |
Privileged administrator roles grant access to manage directory resources, change security settings, and view restricted data. Misuse can lead to security risks, so they should be assigned carefully.
| Role | Can Do | Can’t Do |
|---|---|---|
| Owner | Grants full access to manage all resources, including the ability to assign roles in Azure. | Nothing |
| Contributor | Grants full access to manage all resources but does not allow you to assign roles in Azure, manage assignments in Azure Blueprints, or share image galleries. | Assign roles to users / modify roles |
For example, if you have a lab manager who is not the owner of the Azure subscription, they could get the highly privileged "Contributor" role, granting them access to manage all resources. If you have a student, however, who will use Azure for machine learning projects, then starting them with the "AzureML Data Scientist" role may be a better fit than giving them full access to manage all resources in the subscription.
Start with minimal permissions and increase access if needed.
Creating Custom Roles#
After you have looked over the various built-in roles within Azure and cannot find a role that matches your unique needs there is the option to create custom roles . You can either modify one of the built-in roles or build from scratch. Since building a custom role within Identity Access Management is bit complex, we recommend taking this option only once you have confirmed none of the built-in roles or combinations of roles work for you.
Resources and Resource Groups#
The core of Azure are the resources. These are specific instances you create of Azure’s different services: AI implementations, databases, networks, virtual machines, etc. Resources must be organized into groups. These are called Resource Groups and serve as an organization device. You can, for example, set up different budgets for different resource groups.
From Azure’s learning materials :
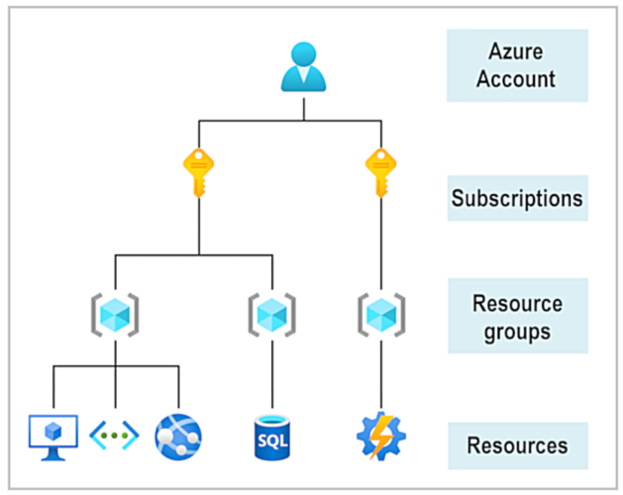
Resources commonly used for research include:
AI and Machine Learning: Azure AI Services, Azure OpenAI Service, Azure Cognitive Services
Storage: Blob Storage
Compute: Virtual Machines (Compute Engine)
Databases: Azure SQL DB, Cosmos DB
Creating an Azure Resource Group#
Every Resource must be in a Resource Group. You can create a Resource Group before creating a Resource, or you can create a new Resource Group at the time you create a Resource. We recommend creating a Resource Group before creating a Resource so that you can name it and set it up in an intentional way.
You can create a Resource Group by following these steps:
Step 1 - Go to the Resource Groups page. Starting at the Azure portal, either type “resource groups” in the search bar, or click on the resource groups icon in the Azure Services section. Then open Resource Groups.
Step 2 - Once you’re on the Resource Groups page click “+ Create”
Step 3 - Enter project details. It will ask you for subscription, resource group name, and region. Below is a description of these.
Subscription: The subscription in which you want to build the resource group. This sets which subscription gets billed.
Resource Group: Create a name for this resource group.
Region: is a geographical area where Azure data centers are located. Select a region where you want this resource group to be placed. Not all regions have access to all services, so if you want a particular service, you’ll need to ensure it is offered in your closest region, and if not, switch to the closest one that offers it. For example, if you are looking into specific OpenAI models, consult this table . Northwestern users should use as a default the North Central US region, since it is located in Illinois. If you are in the Qatar campus, or need to use a region outside of the US, contact Northwestern IT Cloud Operations at azurecloudops@northwestern.edu for approval, since Northwestern automatically restricts regions outside the US.
Step 4 - (Optional) Add tag/s to help with Organization. You might tag things by project, owner, or indicators for whether resources are production (and thus should not be deleted without review), development (delete with caution), or test (can be deleted at any time).
Step 5 - Review your resource group creation and click “Create”.
Then, when you create a specific resource, you can select this resource group during the creation process.
You can move resources from one resource group to another. For details on how to do that see the Azure documentation .
Multi-Resource Services#
Be aware that if you create a resource by selecting a pre-built Azure service, it may create several supporting resources. For example, when creating an AI system that will access your data and extract information for it, you may need storage, search, and AI resources, some of which can be expensive if not configured properly or deleted when no longer in use.
Deleting Resource Groups and Resources#
Some resources can be stopped when not in use to stop accruing costs, but others need to be deleted.
If you delete a resource group, it will delete all resources in that group as well.
To delete a resource group and all resources in the group:
Step 1 - Go to the Resource Group page in the Azure portal.
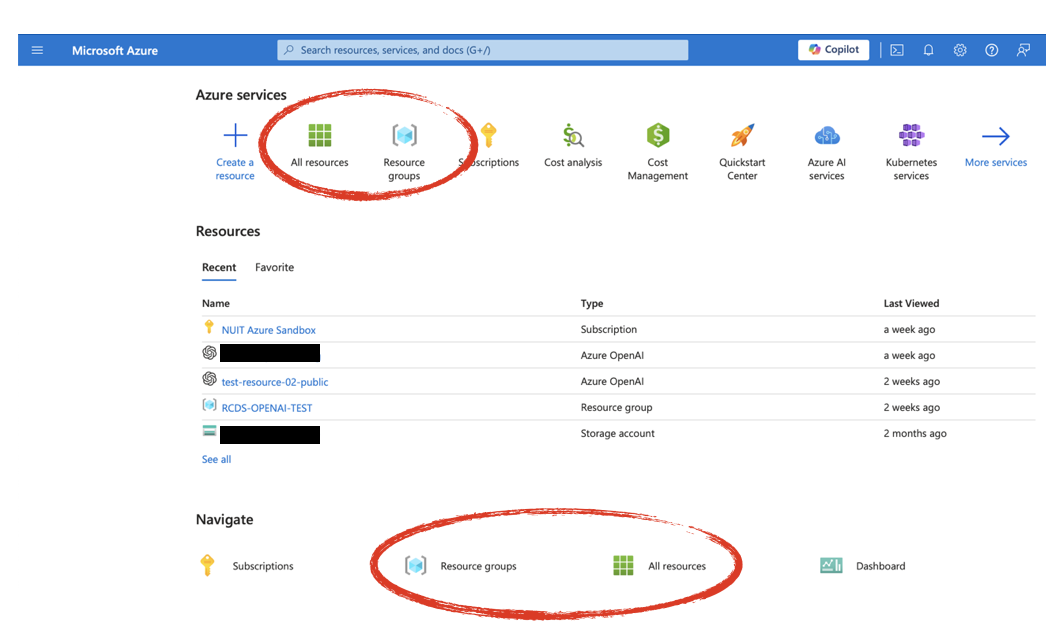
Step 2 - On the Resource Group page, click on the name of the group you want to delete to open a detailed view page.
Step 3 - On the top bar of the detailed page, you will see the option “Delete Resource Group”. Click on it.
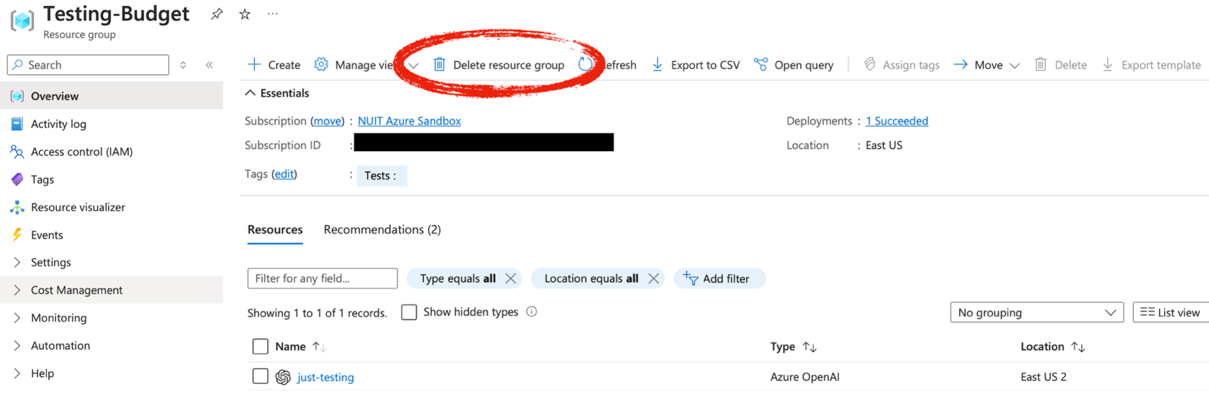
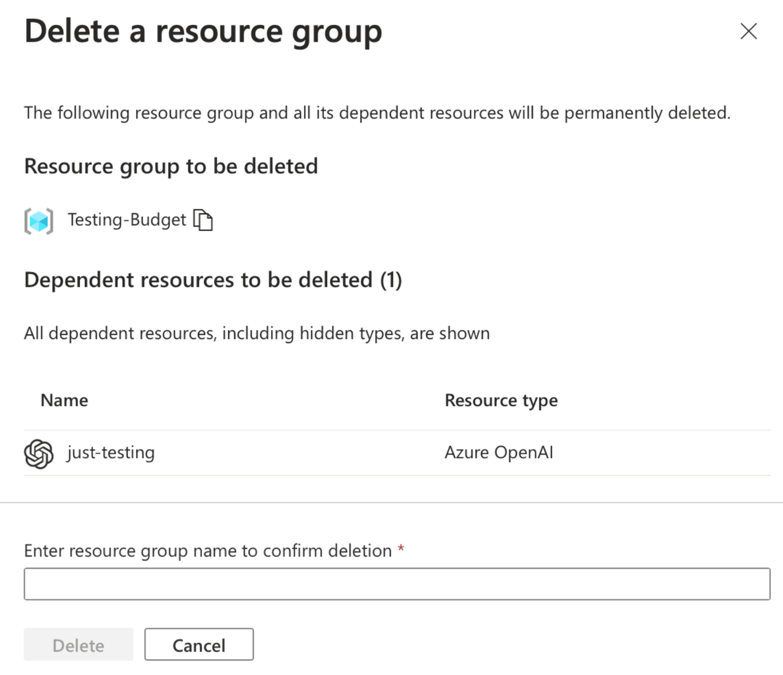
Step 4 - The resulting page will show you which resources will be deleted with the resource group. You will have to confirm deletion by typing the resource group’s name before it actually deletes it. Once you confirm deletion it may take several minutes to complete.
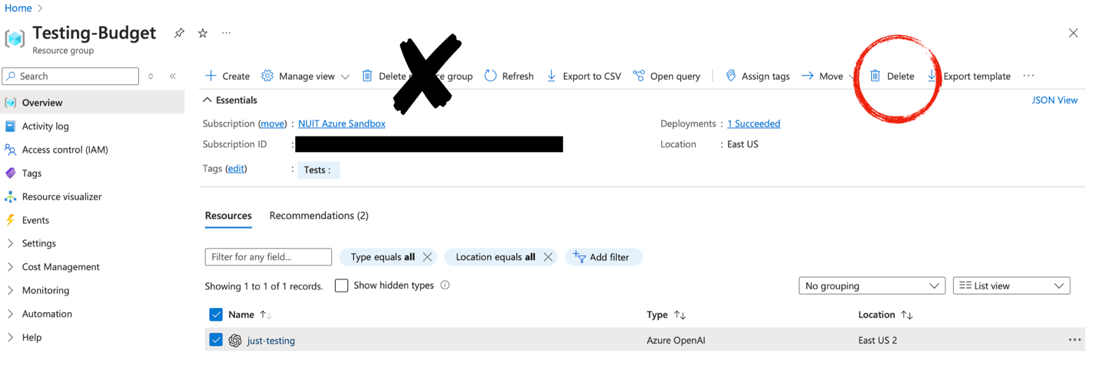
To delete a single resource:
Step 1 - From the Azure portal Home page click on the “All resources” option.
Step 2 - On the page listing all resources, check the box next to the resource you want to delete. Click the “Delete” button, not the “Delete Resource Group” button.
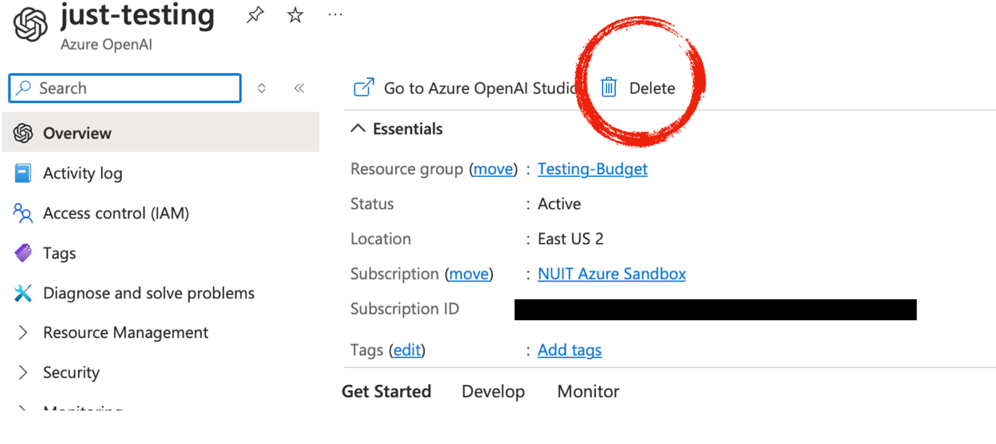
You can also delete a resource if you click on it directly and you find yourself on its information page. If that is the case, just click on the Delete button.
Managing Costs#
It is extremely important when using cloud services to keep an eye on incurred charges and to set up a budget. There are some resources in Azure that will keep charging you even if you are not actively using them, which may result in unexpected costs. Therefore, we recommend you delete any resources that are easily replaceable as soon as you finish using them.
The decision to delete resources differs from resource to resource. For example, for data storage, you need to keep storing your data even if you are not actively using it, so it should not be deleted unless you have a backup and truly won’t need this data anymore. In contrast, if you deploy a service like Azure AI Search, you may only need it once. Delete it when you are done using it to avoid ongoing costs.
Cost Analysis#
Azure has a built-in tool, Cost Analysis and Budgets, to help you monitor costs. Open the detailed page for a Resource Group and then find the Cost Management subsection in the left menu. It has a Cost Analysis option, which will show you incurred charges.
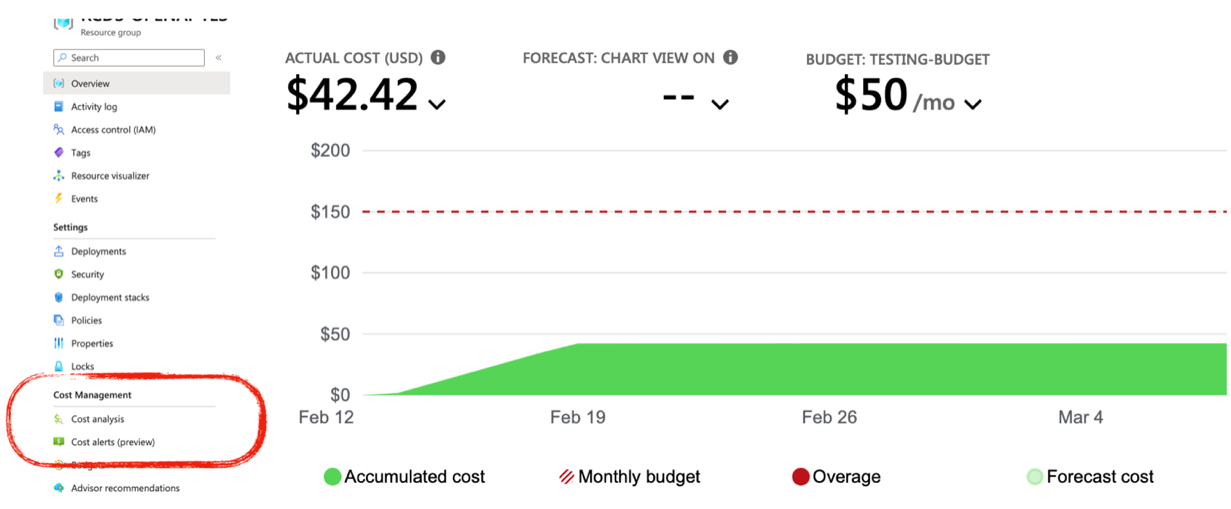
The main graph shows costs over time. You can change the period view in the options bar just above the graph. Below the graph you will also see costs split by services, location, and specific resources. Check this section to make sure you are still using any resources that are incurring costs.
We highly recommend you check Cost Analysis on a regular basis. In particular, after you have created a new resource you are not familiar with, check it every day to make sure there are no unexpected charges.
Budget#
You can create budgets to help you track and manage costs. There is a “Budget” option in the “Cost Management” section in the left menu when you have a resource group page open.
By default, you won’t have any budgets. You can create one by clicking on the Add button on the Budget page and fill out the details. A budget helps you get notifications via email and manage costs more effectively, however, it won’t stop the services automatically and it does not enforce spending limits. You can still go over budget.
Additional Budget Monitoring Tool: KION#
As part of the Northwestern cloud account onboarding process, the owner of the Azure subscription has access to KION, a cost and budget tool that helps track expenses. KION is not part of Azure, but Northwestern University provides free access to it: KION login (Chrome required). The account owner can give other users permission to KION through the Cayosoft group management tool.
Pricing#
Prices for Azure services are listed on the Azure website . Prices may vary by the region the resources are deployed in. Note that you will not be able to access most free Azure resources once you have a paid Northwestern subscription set up.
Many resources are billed based on the number of hours a resource is allocated, whether or not it is actively used. If you create a resource that uses data storage or has reserved computational capacity, you will be charged for the time that resource is provisioned, even if it’s not being actively used. Azure AI Search is an example of such a resource.
Other resources, such as those that listen for specific events or API calls, may charge based on actual use or by allocation time – it varies by resource.
Azure has a pricing calculator with examples. Note that you may need a combination of resources to support your workflow. For example, if you’re creating a database, you will also likely want to store backup snapshots of the database, and the cost of those backups is not part of the pricing for the database itself. If you need help figuring out pricing, don’t hesitate to contact us at researchdata@northwestern.edu .
Network Security#
Many resources in Azure have network security settings that determine how the resources can be accessed. Sometimes these settings are part of the resource creation process. For other resources, they may have a default network security setting which you can change after resource creation by going through the Azure portal; the “Networking” option is under the “Resource Management” menu when you have a resource open in the portal.
Network Access Options#
For many resources, there are three options for network access:
All networks
Access Level: Your resource can be accessed from anywhere, including the public internet. Some services, such as Azure AI Services, still require an API key or other credentials to be used.
Security: This is the least restrictive and broadest form of access. It is the most vulnerable to attempts to scan public cloud resources for security flaws in order to gain access to them.
Use Case: Making your resource accessible so that anyone can use. Note that resource owners, not users, are billed for the usage.
Selected networks (recommended)
Access Level: By default, this will restrict access to only be allowed from other Azure resources that you assign to the same Virtual Network as this resource. This setting can also be used to restrict access to requests coming from a specific IP address or range of IP addresses, such as Northwestern’s network. Below we show you how to do this.
Security: This option can allow access from places you expect (such as your home or the Northwestern network) while limiting opportunities for others to accidentally gain access to your resources.
Use Case: If you are working with non-public research data, this is the minimum recommended security setting.
Disabled
Access Level: Your resource can only be accessed by a specific endpoint/s. Examples of endpoints include a specific server, or a virtual machine.
Security: The most restrictive and secure option.
Use Case: Useful for when you are working with data that has high security requirements or specific data use agreements. Such situations should be addressed with IT to ensure that all requirements are being met.
Configure Selected Networks#
The “Selected networks” option is the recommended choice for most resources. This option allows you to restrict access to your resource by specifying which IP addresses can connect to it.
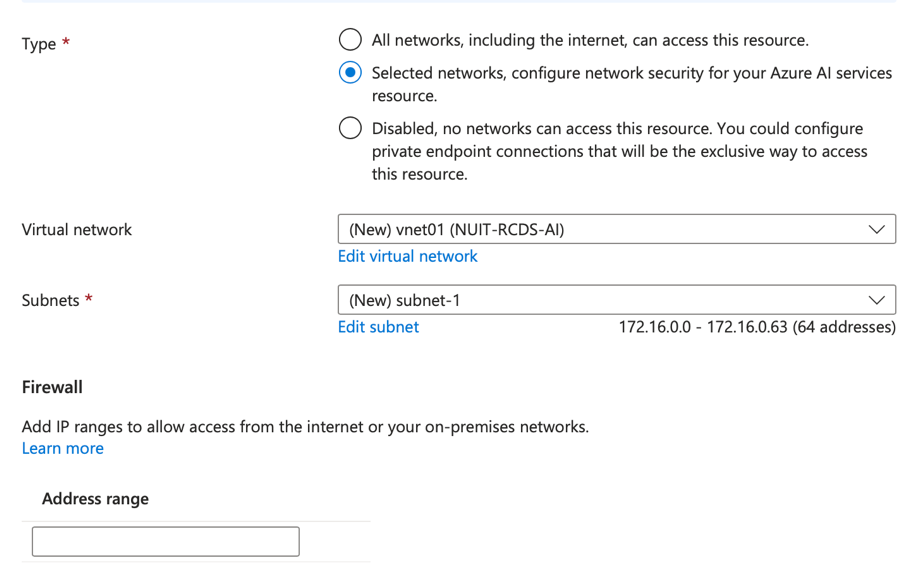
Once “Selected networks” is chosen, three additional sections will appear: Virtual Network, Subnets, and Firewall. For most users, the default settings for Virtual network and Subnets will suffice, which create a new virtual network and a new subnet. A virtual network is a network inside the Azure cloud that connects your resource to other Azure resources.
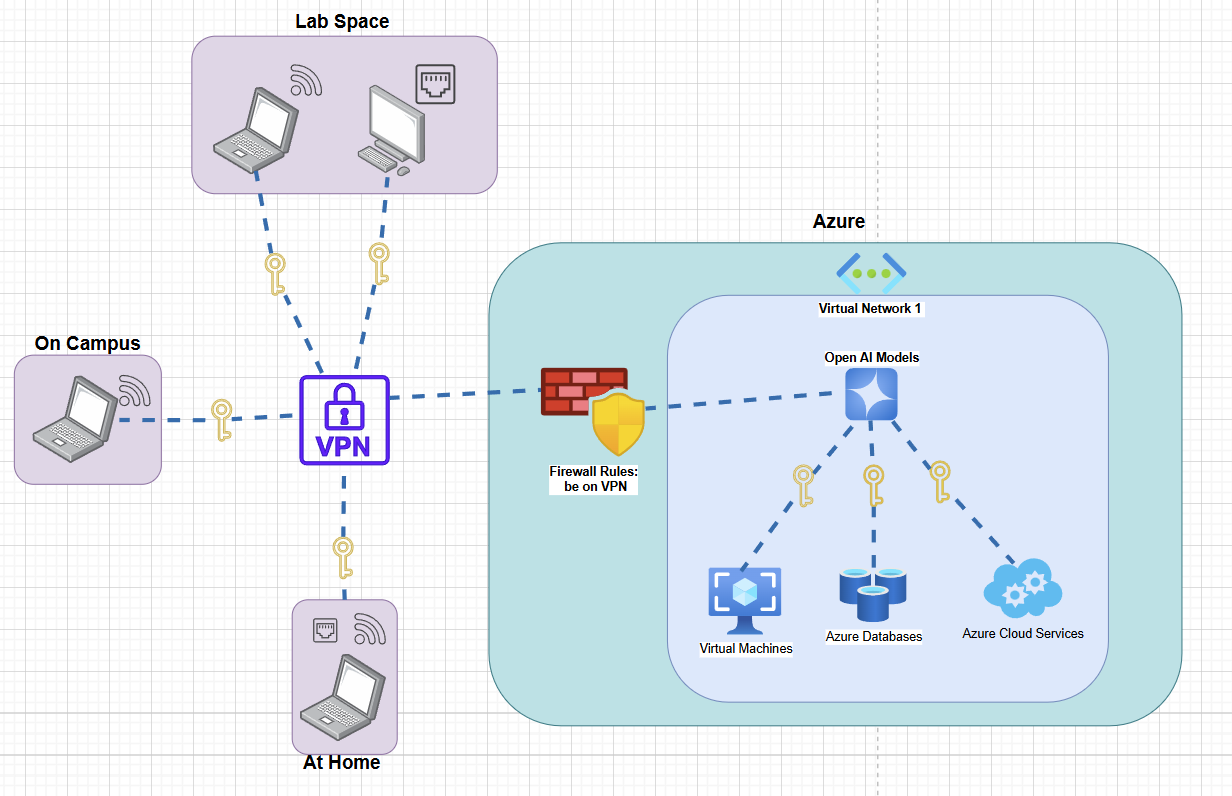
With only a virtual network, you can only access your resource from other Azure resources. The Firewall section is used to provide access to networks outside of Azure, such as the Northwestern network. Access is provisioned based on IP addresses .
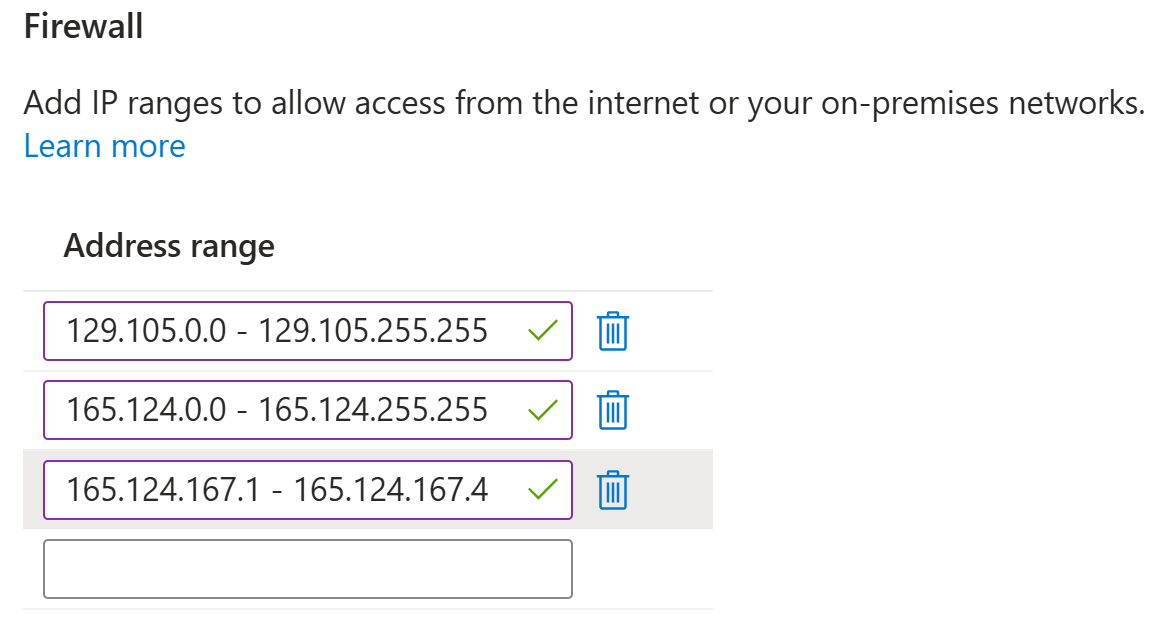
| Network | IP Address Range |
|---|---|
| Northwestern Global Protect VPN | 165.124.167.1 - 165.124.167.4 |
| Evanston campus Wired/Wireless | 129.105.0.0 - 129.105.255.255 |
| Chicago campus Wired/Wireless | 165.124.0.0 - 165.124.255.255 |
Enter one or more of the following IP ranges in the Firewall section. You can add any single range, or multiple ranges, depending on where you need access from.
Off-campus access (recommended): Use the Northwestern GlobalProtect VPN range 165.124.167.1 – 165.124.167.4. This avoids relying on a home IP address, which can change over time.
Evanston campus access: Add the Evanston campus wired/wireless range 129.105.0.0 – 129.105.255.255. This also covers Quest systems, since Quest IPs fall within the Evanston range.
Chicago campus access: Add the Chicago campus wired/wireless range 165.124.0.0 – 165.124.255.255.
If you work from multiple locations (for example, both campus and VPN), add all applicable ranges so you can connect from each location.
Using Firewall rules adds an extra layer of security by allowing only those connected through the designated networks to access your resources.
Protection Against Leaked Keys: Even if your access keys or credentials are leaked, they won’t be usable by those who do not have access to the Northwestern network.
Access Control for Departed Users: If you limit access to the Northwestern Global Protect VPN only, people will lose access to your resource once their NetID is deactivated because they will no longer be able to connect to the VPN.
